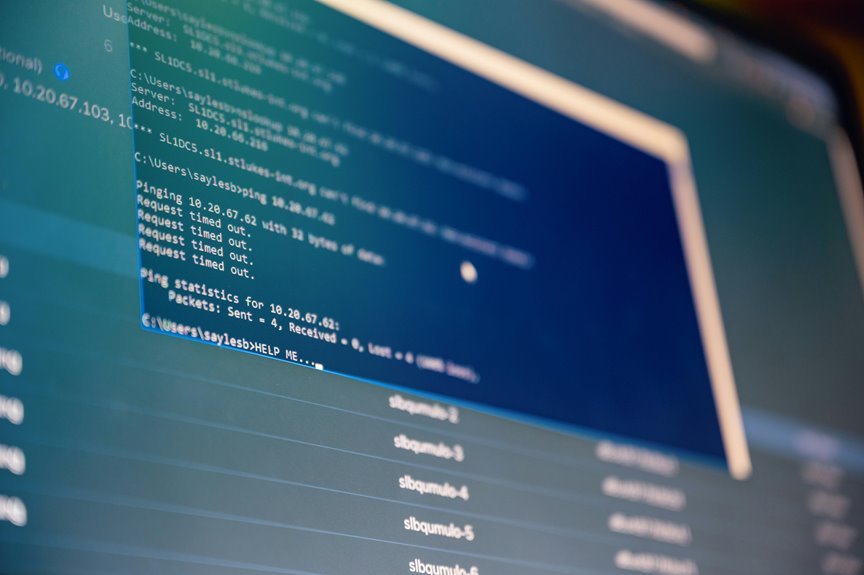
10.70.122.5589: System Address Analysis
The address ‘10.70.122.5589’ presents a unique case in system address analysis. This notation raises questions regarding its validity and implications for network configuration. Understanding its structure is essential for effective network management. Moreover, exploring its role in device tracking and security can reveal insights into optimizing performance. The complexities surrounding such addresses warrant a closer examination of their impact on organizational efficiency and data integrity.
Understanding the Structure of System Addresses
System addresses serve as critical identifiers within computational architecture, facilitating the organization and retrieval of data in memory.
Address formats vary, influencing how data is structured and accessed. The address hierarchy further categorizes these formats, allowing for efficient management and allocation of resources.
Understanding these components is essential for optimizing system performance and ensuring the seamless operation of complex computational environments.
Significance of ‘10.70.122.5589’ in Network Management
The address ‘10.70.122.5589’ highlights the complexities of network management, particularly in environments that utilize Internet Protocol (IP) addressing.
Effective address identification is crucial for maintaining network security, as it enables precise tracking of devices and traffic patterns.
This specific address underscores the need for robust management protocols to mitigate risks associated with unauthorized access, ensuring efficient network operations and safeguarding user autonomy.
Applications and Implications for Network Performance
While network performance is influenced by various factors, the effective application of IP addressing significantly enhances overall system efficiency.
Optimizing IP configurations reduces network latency, facilitating quicker data transmission.
Additionally, integrating robust security protocols within the addressing framework ensures data integrity and confidentiality.
These applications are crucial for maintaining high-performance networks, particularly in environments requiring both speed and security in information exchange.
Conclusion
In conclusion, the illustrious ‘10.70.122.5589’ stands as an emblem of network complexity, a digital Picasso in a gallery of IP addresses. While some may dismiss it as just another number, savvy network managers recognize its potential to transform chaos into order, optimizing performance with a mere flick of configuration. As organizations chase the ever-elusive goal of perfect data transmission, perhaps the real question remains: is it the address that needs analysis, or the analysts themselves?